- “Ducktail” Hackers Target Facebook - September 28, 2023
- Okta Breach: Super Admin Hack - September 24, 2023
- Rackspace: $10.8M Cloud Shift - September 23, 2023
Surveillance has emerged as a highly pertinent concern in recent years. Millions of individuals have fallen victim to spying through webcams, microphones, or malware. Beyond the profound discomfort this notion evokes, it carries inherent risks, including the potential for blackmail, ransomware attacks, or loss of valuable files. In this article, we will discuss how hackers can spy on you.
Webcam on a Phone`s Camera

Webcam spying is perhaps the most popular method of spying. It’s pretty easy for a criminal to hack your camera, especially if you`re not careful with cyber hygiene.
When an attacker obtains access to your smartphone, they may be able to operate your camera, turning it on and off, gazing through its lens, collecting photographs, or even listening in through your device’s microphone. The silver lining, although a shaky one, is that modern gadgets include an indication light or symbol that lights when the camera is activated.
If this light appears suddenly, especially when none of your trusted programs are intended to be using the camera, it might indicate a problem. When a hacker manages to break your device’s security, their motivation is usually to obtain particular information rather than to engage in widespread monitoring of your actions. It is crucial to highlight, however, that hackers frequently target not only people, but also data from security cameras maintained by huge organizations.
In one reported case, this strategy gave them access to a large library of footage from 150,000 security cameras located in a variety of contexts, including hospitals, warehouses, and penal facilities. However, it is not unusual for hackers to target specific persons. Malware and other dangerous files can get illegal control of your camera, as well as expose passwords or crucial information kept on your phone or computer. This emphasizes the importance of having strong cybersecurity policies to protect both personal privacy and sensitive data.
Microphone

Another typical tactic used by hackers is the use of microphones for spying. Yes, there are people who can compromise your operating system and gain control of your microphone, allowing them to eavesdrop on conversations and steal private data. Indeed, as German researchers have revealed, the scope of this extends beyond basic eavesdropping. Almost all recent devices include built-in microphones. How do you find out if they are being used? Microphones, unlike webcams, lack indications, rarely provide on-screen notifications, and are not as readily covered.
Even if you talk softly, muffled speech may be picked up, especially if you speak loudly.
One example is the use of RATs, which stands for “Remote Access Trojans.” These harmful apps allow hackers to remotely manipulate a victim’s computer. They can dodge security software and function in the background by often exploiting zero-day flaws. Once active, these RATs may capture audio from the user and their surroundings and send it back to the hacker through compressed audio files or encrypted streams.
Even in highly guarded government and business organizations, RATs have been discovered, raising worries about the quick disclosure of secret data. The proliferation of Voice over Internet Protocol (VoIP) phones, such as Skype, has aggravated the problem by increasing possible vulnerabilities. To summarize, whether you’re a home user or a company owner, the threat of audio RATs is real and relevant.
Screen Monitoring

Hackers have a strong preference for infiltrating your device with malware and trojans. One of their preferred methods is to install keyloggers on your phone. This nefarious tactic allows a hacker to painstakingly trace your digital activity and secretly collect the login information you use for multiple websites and applications.
Hackers’ use of keyloggers and related tracking software introduces a very intrusive tactic. These programs secretly capture a variety of data, ranging from your search searches and login credentials to passwords, credit card details, and other sensitive information, by recording keystrokes flowing from your phone. One unsettling aspect is that someone might possibly see your cell phone’s activities without ever physically touching it.
Another method that hackers use is mobile spyware, often known as stalkerware. This approach requires putting hidden software on your phone to monitor a wide range of data, including calls, text messages, emails, geographic location, photographs, and browser history. The troubling fact is that in today’s digital ecosystem, attackers may delve into your most intimate and private conversations, possibly jeopardizing both your security and your privacy.
How Hackers Get Access to Your Device?

Before hackers can spy on you, they need to get access to your device. Nowadays, not many people take cybersecurity seriously, making it easier for cybercriminals to get access to your device. Below are the methods of how criminals might gain this access.
Phishing
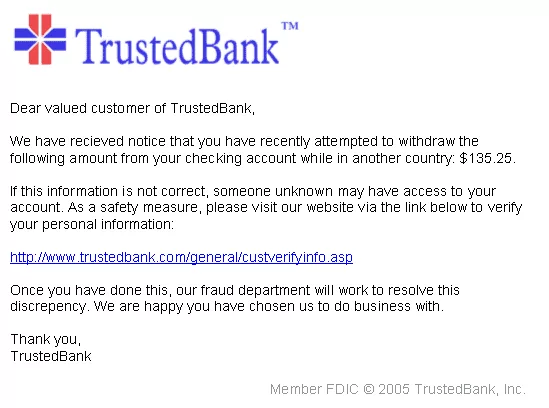

Phishing is a devious technique used by attackers to deceive people into unintentionally downloading malware. This method is based on the deception of emails or messages that closely resemble authentic correspondence. These deceptive communications frequently contain dangerous components, such as malicious URLs or attachments. When these elements are engaged with, they threaten the security of your device by allowing compromise.
Remote Access Trojans (RATs)

Remote Access Trojans (RATs) are a type of malware that provides attackers extensive control over your device from a remote location. This advanced strain of malicious software gives hackers unlimited control over your device, thereby turning it into a puppet under their direction. RATs infiltrate your device by many techniques, such as phishing emails, corrupted software, or flaws in your operating system, and then embed themselves in your system invisibly. Once firmly established, they open a covert communication link with the attacker’s command and control server, enabling remote management.
The level of control provided by RATs is both broad and intrusive. Attackers can remotely activate your device’s webcam, thereby transforming it into a covert surveillance tool that collects visual data from your surroundings. In a comparable manner they may get access to your device’s microphone, allowing them to intercept audio feeds and listen in on conversations without your knowledge. These features extend to monitoring your total digital activity, such as keystrokes and program usage, as well as file access and network connections.
Hacked Wi-Fi Networks
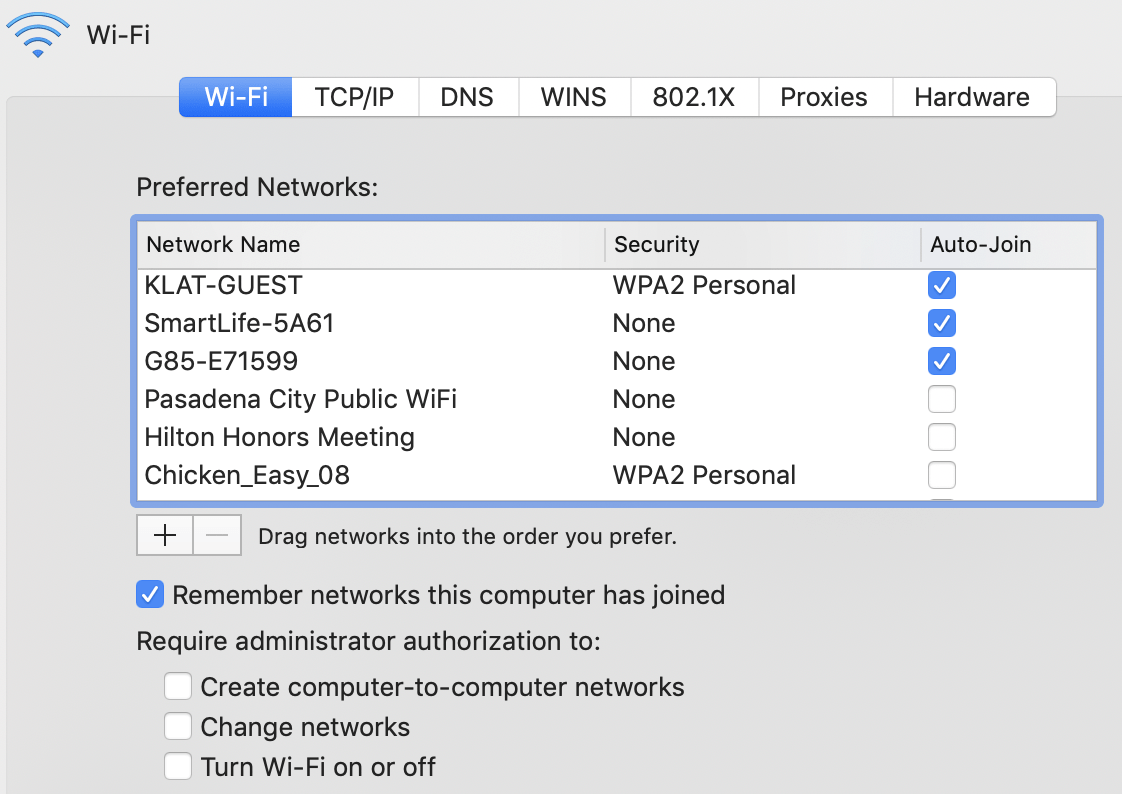

Engaging with deprived Wi-Fi networks exposes your device to a serious and immediate threat to its security, partly due to the inherent flaws that these connections have at their core. When a user connects to an insecure or hacked Wi-Fi network, it creates a channel that malicious actors may expertly follow, giving them a prime chance to hijack the network and control the data flow that is being transmitted via it.
Physical Access


Potential attackers have a wide range of options to carry out espionage or jeopardize the security of your device if someone can physically access it. Your gadget is vulnerable to a wide range of malicious acts when an unauthorized person comes within close proximity of it. These include deceptive practices including covert spyware installation, hardware keylogger encapsulation, and the introduction of malicious devices.
Weak Passwords
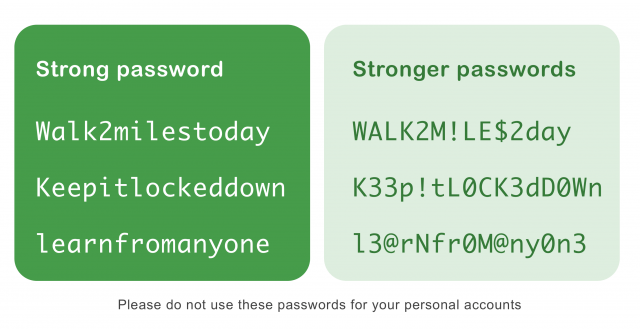

Making use of weak passwords is a dangerous practice that increases the susceptibility of your entire digital environment. Your passwords’ predictability or lack of sufficient complexity provides a vulnerability that prospective attackers can take advantage of with negative results. By acting as a point of entry for illegal access to your online accounts, this vulnerability opens your device up to a wide range of complex threats.
Malware

Malicious software, often known as malware, is a ubiquitous and cunning threat that looms large over your device’s security. This powerful malware is distinguished by its capacity to covertly access your device through a variety of entry points. Infected email attachments, downloads from dubious websites, and, unsettlingly, even corrupted software updates are included in this category. Once malware takes hold, it triggers a series of events that provide hackers the tools they need to manage your device remotely. Your webcam and microphone are included in this sinister control, which eventually jeopardizes your security and privacy.

