- Top 7 Darknet Markets and What You Can Find There in 2023 - September 18, 2023
- Can You Cheat a Drug Test? - August 17, 2023
- How Do Police Dogs Recognize Drugs? - August 17, 2023
Hackers found a new goldmine called cryptocurrency. It’s pretty easy to steal it, it’s highly profitable and the risks are usually minimal. Currently it`s the time when dark web cyber security is at high demand.
Fake Crypto Exchanges
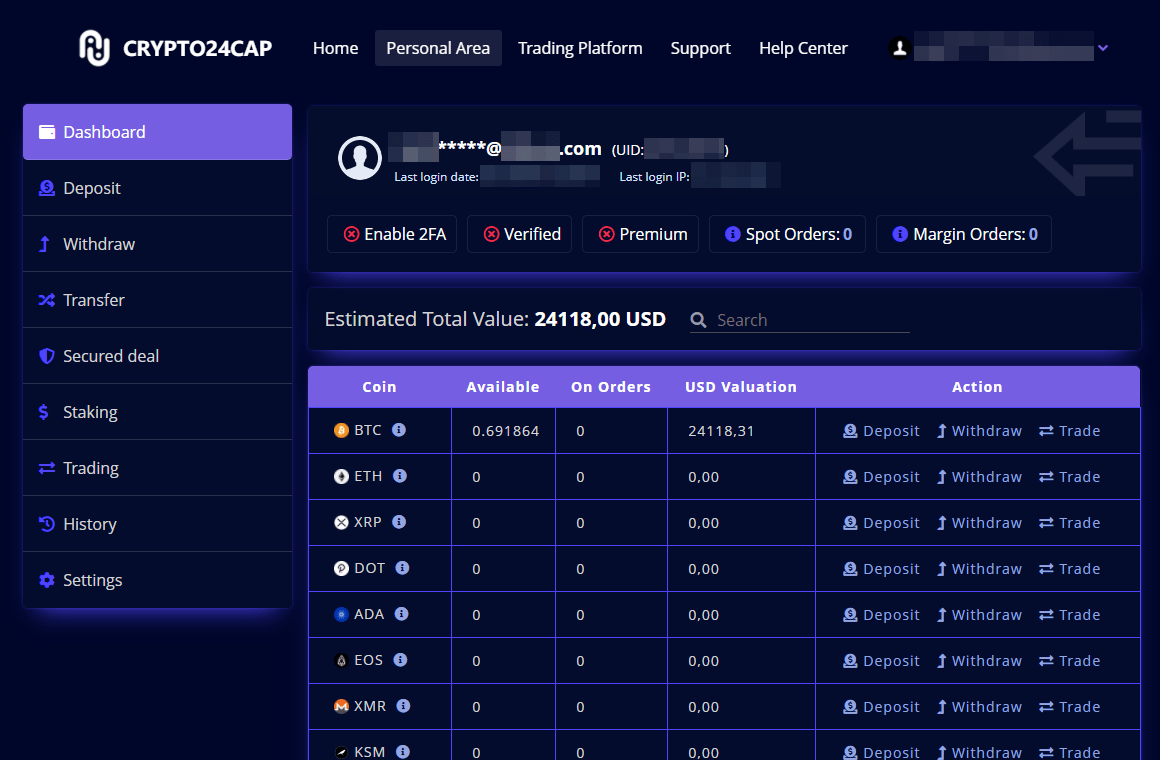

Hackers often use fake crypto exchanges to steal crypto. Moreover, they might steal your credentials as well if you try to turn money into fiat. When you exchange the currency, you send your bitcoin to a certain address, which can belong to the criminals. In this case you will never get your currency back. That’s why it’s important to only use trustworthy and safe crypto exchanges.
Phishing
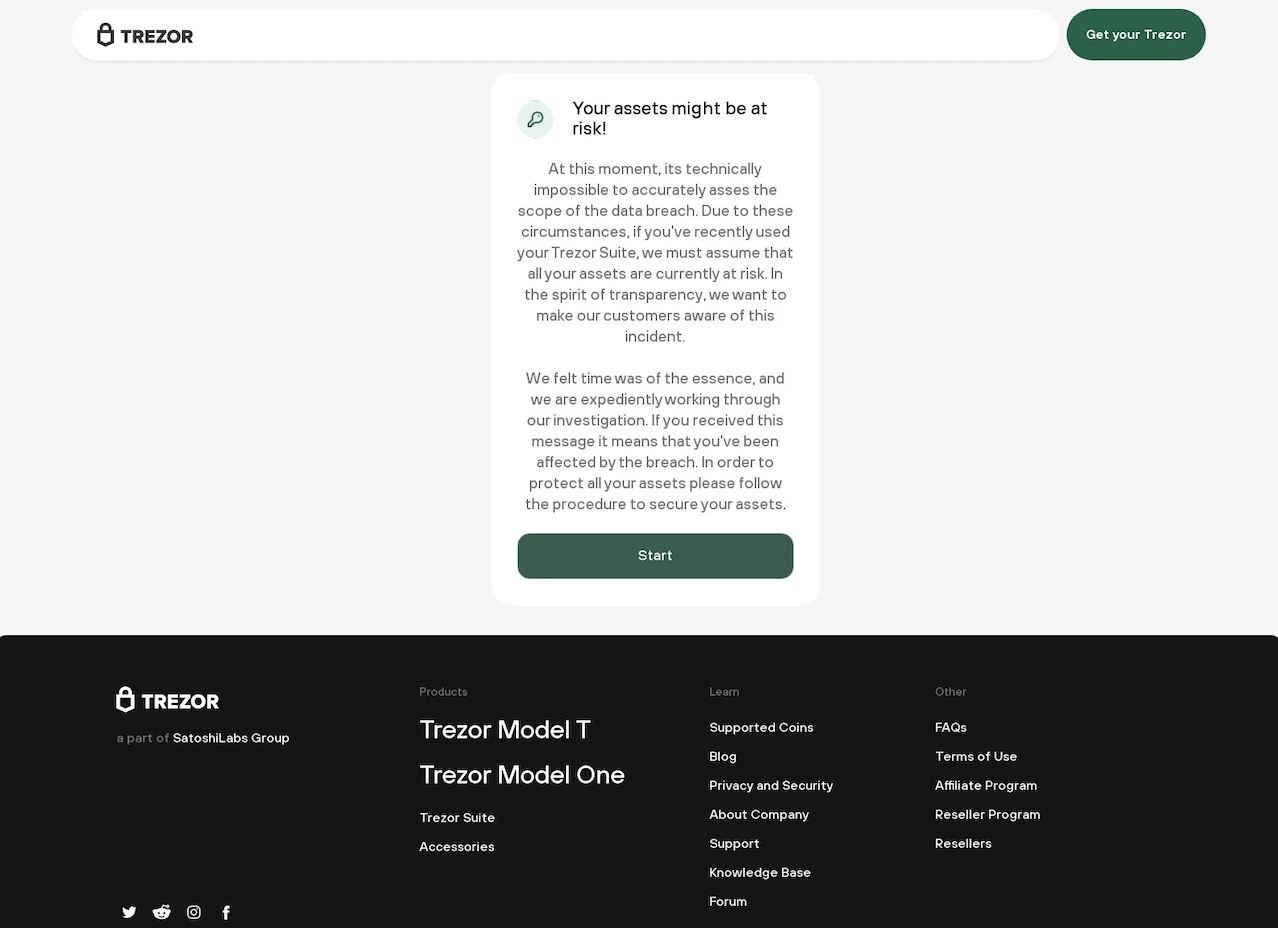

It’s necessary to bring phishing awareness because your data might be used by hackers or phishing scammers to construct “targeted” phishing assaults. They may simply send an SMS to Tommy stating, “Hey Tommy, we spotted somebody withdrew $5,000 from your account, please click this link and reach customer service if it wasn’t you,” because they now know he uses the exchange “X.”
Trezor, a company that makes hardware wallets, alerted its customers to a phishing assault in March that required users to enter their wallet recovery phrase on a phony Trezor website in order to steal investors’ money. Attackers masquerading as Trezor used the phishing effort to contact victims by phone, text, or email and inform them that their Trezor account has had a security breach or other suspicious activities.
Dark Web Markets
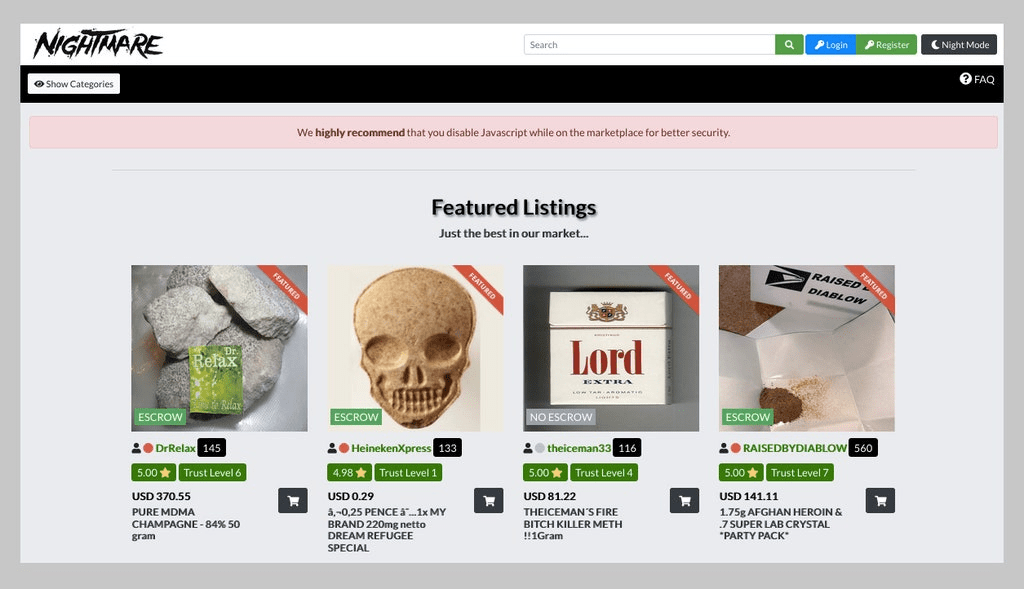

Almost entirely, cryptocurrencies like Bitcoin are accepted as payment methods on dark web marketplaces. The possibility of issues is increased because these websites are hidden from governments and authorities. For instance, Mt. Gox was the target of a previous incident in which more than $100 million in Bitcoin was taken. Some of these websites may appear to be marketplaces, but they are actually traps put up by hackers. Users’ keys are taken when they complete a transaction.
Therefore, it is especially crucial that you plan your actions and where you will carry them out. This holds true for the whole internet, not just the dark web. A website that is open to all users may experience the same situation. Because they utilized a fraudulent website created by crooks, thousands of individuals in the past lost Bitcoin. Users are drawn to these kinds of websites through phishing. Additionally, be aware of hackers forum dark web as it holds similar danger.
Crypto Malware
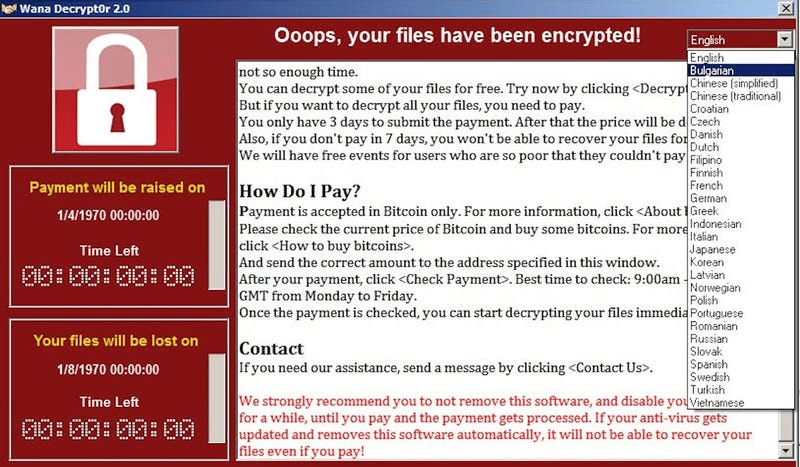

The development of cryptocurrency tempts hackers to target hot wallets. Trojans let attackers steal data and quickly move funds by shifting crypto-malware attacks. Because these blockchain transactions are irreversible, it is difficult to get back money that has been taken. With new viruses, security concerns for browser crypto wallets (like MetaMask) are getting worse. An improved trojan called “Mars Stealer” targets more than 40 browser wallets and steals private keys.
The virus targets private key files to covertly steal data and spreads through file hosting, torrents, and other channels. Mars Stealer may be purchased for $140 on the Dark Web by criminals. Its current focus is on Chrome’s hot wallet credentials. Since 2017, “Clipper” has exploited the use of the clipboard by substituting fake crypto addresses. Complex addresses cause users to inadvertently send money to hackers.
How to Protect Yourself?

Microsoft has taken preemptive measures to protect customers from the dangers of cryptocurrency wallet malware. The business has presented a number of helpful advice targeted at strengthening customers’ hot wallets, which are digital wallets connected to the internet, as part of its commitment to boosting security:
- When a user isn’t actively trading, keep hot wallets closed and disconnect any websites that are linked to the hot wallet;
- Implicate dark web monitoring tools;
- Use best crypto mixers;
- Never copy and paste password information, and avoid storing private key information in plain text (which is readily stolen);
- Learn about dark web cybersecurity;
- Every time a transaction is finished, end the browser session;
- Avoid telegram crypto scams, especially with dark web links;
- Watch out for shady links to wallet websites and applications, and double-check any approvals and transactions with your crypto wallet;
- Avoid disclosing seed words or private key information, and look for wallets that have multi factor authentication;
- Utilize hardware wallets with offline private key storage;
- Verify again the complete file extensions of the files you download.

